In my yesterday blog post I discussed a bit of software bugs in shKGA. Bugs cause applications to act erratically, in a way the developer didn't mean for it to act. This can cause crappy UX or non-functioning features. This is the main area of concern when I build apps for my own fun. In my 9-5, I've also briefly touched on me and my team squashing security vulnerabilities for a few months to bring our app the the cloud. I have a breadth of experience relating to technology, so let's see what the bots want and how bugs relate.
I talk of bots and bugs a lot, if you look at a bug enough if can tell you about where it lives in the application. It can give you clues (like trying to solve a Sudoku puzzle) to help you find how to fix it. This is the perspective of a software developer, but similar footing in the app ecosystem can nag one to look at it further, even if they're not the developer responsible for maintaining the app. A rogue actor, including bots, could use the bug as leverage to perform a privilege escalation attack. This could allow access to all the data of the site, or depending on configuration, even leave the developer's own accounts up for sale. The rogue actor can then decide to do what they want with the bounty. If it's a high profile individual, maybe you can black mail them into giving you money? If it's an interesting database, maybe the data can be sold on the dark web? Maybe it's just a flex, and someone puts a piece of code on the site to mine cryptocurrency? The imagination is the limits here, and with 8 billion people on this planet it could get tiring trying to go through all their thoughts and ideas of hacking.
See below this image from Microsoft Azure, it highlights meandering attacks of 6.66k probes since November 11th. I've filtered on the key term "wp", so there might be more but let's explore the image and unpack it a bit to see what the bots are after.
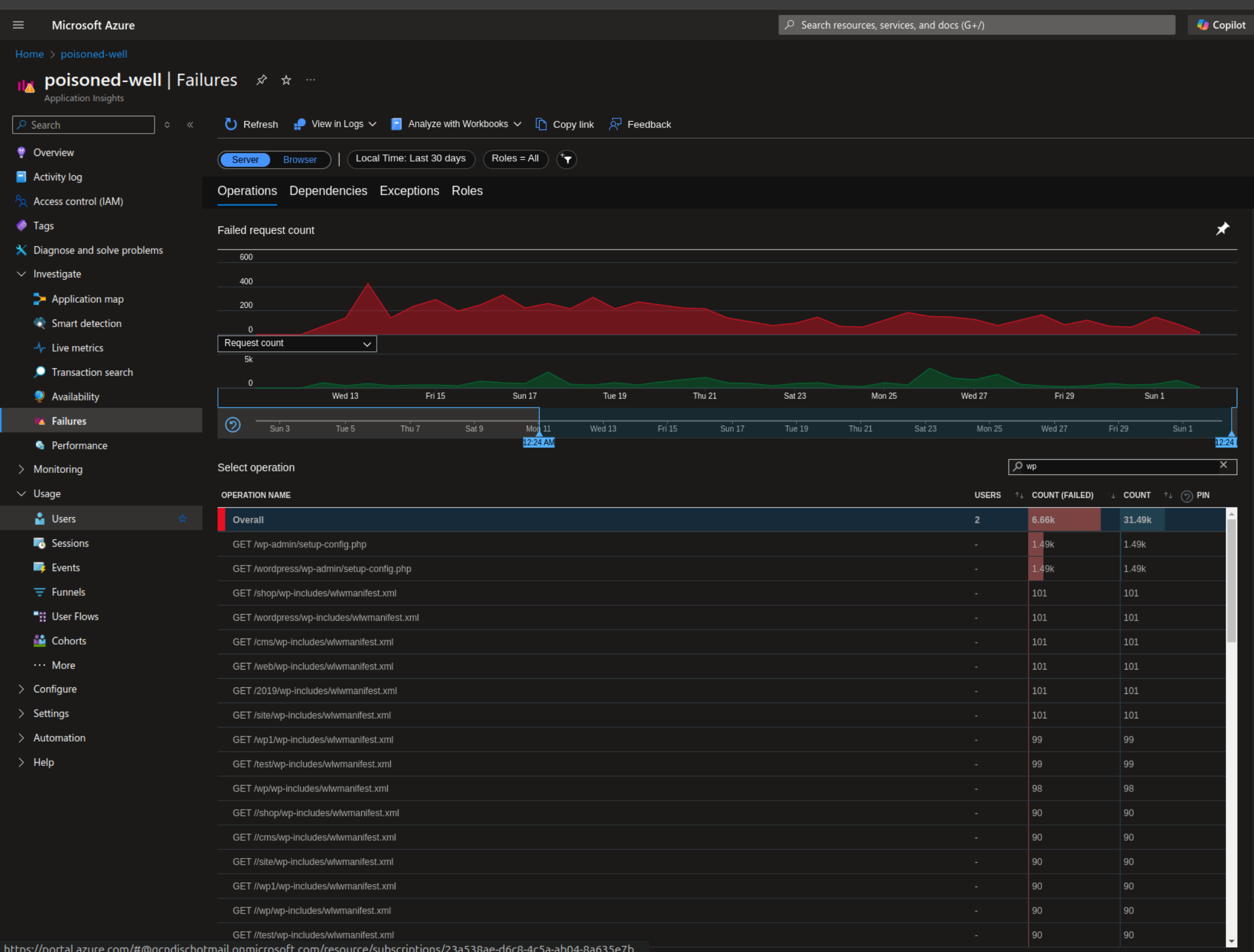
In the above image you can see the Azure Application Insights failures view. It shows a graph of average number of errors, and a list of the most frequent errors. I've filtered for "wp", meaning Wordpress, as this is an attack vector even unskilled hackers can start to gain access. I won't go into great lengths here about all the bugs affecting Wordpress because there's a lot online if you look for it. The reason bots are probing WordPress sites can also be found if you search online, for example from Gemini:
As of February 2024, over 835 million websites use WordPress, which is about 43.6% of all websites on the web. WordPress is a popular content management system (CMS) that allows users to create and manage websites from any computer.
So having that many instances means if even 0.001% is misconfigured in a way to allow hacking, then you have 883 thousand vulnerable instances, which means a lot of sweet sweet candy for wannabe script kiddies. You just find a few instances that are misconfigured, and you can push payloads to infect the visitors of the site. That's a bad day for those people, but even worse day for the owner of the site as they lose their business. If it's their livelihood, they could go without until they can get back online. If it's just a small hobby, like it is for me, it wouldn't be much skin off my back. But I'd feel embarrassed and less than due to my position as a software developer.
No one is infallible, but if the bots get even the most vigilant of us then it's hard to imagine a society where anyone is safe. If you run a Wordpress site, WPScan (you need an API key, and it won't do hacking, but it will tell you if you're WP instance is vulnerable) or similar products can help sus out issues in your site. It's tidbits of info like this is why you should spread this message far and wide, to ensure we have the knowhow to fight the good fight against the poison in our well.
Isaac