Yesterday I was looking into a security feature you can layer onto email with PGP encryption to secure the newsletter of this site when it goes live. I was looking at FlowCrypt which has a browser extension and mobile apps to make this process more seamless for the end user (as PGP is generally an hard technology to use). It requires generating, securing and not losing a private cryptographic signature. If it sounds complex, it's because it is. So researching this bit of tech helps me to understand what issues could arise having many people hold some PGP keys without idea of what that means. PGP or cryptographic signatures of some nature will be important for decentralized identity, which is my main area of research.
FlowCrypt offers a public key directory (similar to a phone book) of person's public keys with part of their software called Attester. Attester simplifies transmissions of encrypted emails, but I've got further reading to understand the security implications of such a solution. I'm also not 100% keen on their license which seems to say they control the system which results in a single point of failure. It also has some weird language but I'm not a lawyer, so who knows.
To those of you close to me, you'll know I picked up a Chinese phone in June, OnePlus Ace 3 Pro. I bought it because it didn't seem a global release was coming soon and it had incredible hardware that is brag-worthy (humble-brag 😎). Yesterday, as any concerned security researcher does, I downloaded the Android app source code for FlowCrypt, built it with Android Studio, and deployed it to my OnePlus. If you're unfamiliar with this process, there's Developer Mode settings in Android that need to be enabled before you can debug applications on the device. When I enabled Developer Mode I was surprised to see this setting enabled by default:
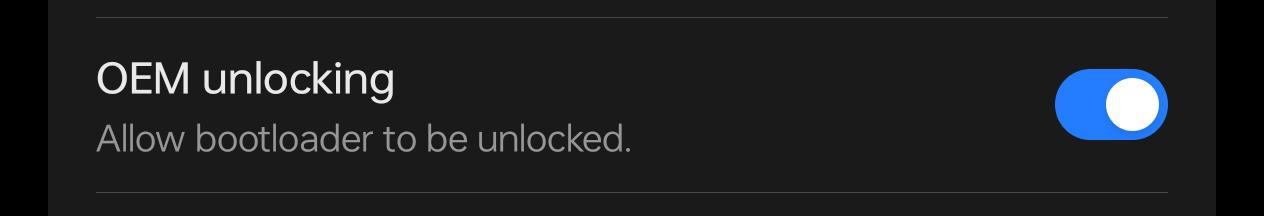
I'll don my tinfoil hat for a second as I explain what this means to you. If I'm correct it means someone in the chain of trust enabled this by default. I did buy this phone from a 3rd party who loaded Google Play services on it, but I did a factory reset and loaded them on myself immediately after receiving delivery. OEM unlocking being enabled by default poses a direct security vulnerability to anyone running a device with such setting enabled. Not only does it disable on-device disk encryption, it also does not protect anyone from loading in code into the bootloader (at least through Android, further bootloader protection can be layered below Android user space and Android OS. Protection can exist in the kernel or bootloader itself).
With OEM bootloader unlocking available, anyone with physical access to your device could in theory copy the device to hack offline without your knowledge. They could put code into the bootloader where it can monitor all network activity, possibly get into your camera or whatever sort of nefarious actions the perpetrator wants. Your imagination is basically the limit.
This is one of the many reasons I switched from M$FT Windows, to Ubuntu Desktop which is a Free and Open Source (FOSS) alternative operating system for computers. All the source code can be downloaded and read with your own eyes, you can independently audit it yourself. Or if you don't have that knowledge, you can sleep easily knowing that it is independently verified that it does what it says it does. There's no background shenanigans that is going on by some rogue engineer (Usually. Supply chain attacks happen unfortunately), or even worse, by the company itself.
This isn't to say there isn't a reason why one might want OEM unlocking enabled, but it's very negligent to keep it enabled when given to an end user. If it was done by the company I bought it from or OnePlus it's gross negligence with corporate sponsorship. It creates a lopsided power dynamic, one that you don't even know exists. Anyone at any point could just snapshot your device and know just as much about you as Apple or Google. It might not be scary on the surface, but I've touched on social-engineering and other possible attack vectors a malicious actor can take. Any bits of information is bread crumbs to getting into your FB account, your bank account or even your mind.
Isaac